
Every business today is digital at its core. From storing customer records to processing online payments, everything runs on systems that are connected 24/7.
But here’s the tough question: Is your business really safe from modern cyber attacks?
The truth is, cybercriminals are changing faster than many businesses can keep up. What used to be simple malware has now turned into sophisticated attacks powered by AI, social engineering, and global hacking groups. One weak link, an outdated system, a careless employee click, or a missed update can open the doors to a full-blown breach.
That’s why understanding the threats and knowing how to defend against them is no longer optional. It’s a survival factor.
Understanding Modern Cyber Threats
The landscape of cyber threats is constantly shifting. Attackers are always one step ahead, finding ways to bypass even advanced defenses.
Rise of AI-Powered Cyber Attacks
AI isn’t just helping businesses; it’s also in the hands of hackers. Attackers now use machine learning to automate phishing campaigns, crack passwords, and even mimic human behavior online. These AI-driven attacks are harder to detect and can spread at lightning speed.
Imagine a system that learns your team’s email habits and sends fake messages that look exactly like your CEO’s style. That’s happening today, and it’s catching even experienced employees off guard.
Growing Impact of Phishing and Ransomware
Phishing emails are no longer clumsy messages full of typos. They’re polished, professional, and often mimic trusted brands. A single click can lead to ransomware locking down entire systems until a ransom is paid.
Small and mid-sized businesses are especially vulnerable, because attackers know many don’t have strong defenses in place. Paying ransom doesn’t even guarantee recovery it just makes businesses a repeat target.
Supply-Chain and Third-Party Breaches
Even if your internal systems are strong, what about your vendors? Supply-chain attacks target partners, software providers, or contractors with weaker defenses. Once breached, attackers can jump into your environment unnoticed.
Think of it as locking your front door but leaving a side window open through a partner system. Businesses that overlook third-party risks are leaving themselves exposed.
Key Vulnerabilities in Business Security
So, where do businesses go wrong? The most common weaknesses usually fall into these categories:
Risks from Legacy Systems and Outdated Tools
Old hardware and outdated software are ticking time bombs. Unsupported systems don’t get security updates, leaving well-known vulnerabilities open for attack. Yet many companies still hold onto them to “save costs,” a decision that often proves far more expensive later.
Insider Threats and Human Error Exposure
Not every threat is external. Employees, whether careless or malicious, are one of the biggest risks. Weak passwords, falling for phishing scams, or misusing data can all lead to costly breaches. Even the best firewalls can’t stop an insider mistake.
Gaps in Continuous Monitoring and Detection
Cyber threats don’t keep office hours. Yet many businesses lack 24/7 monitoring. Without real-time detection, attacks can sit unnoticed for weeks or even months, causing deeper damage before they’re discovered.
How a Cyber Security Company Protects Businesses
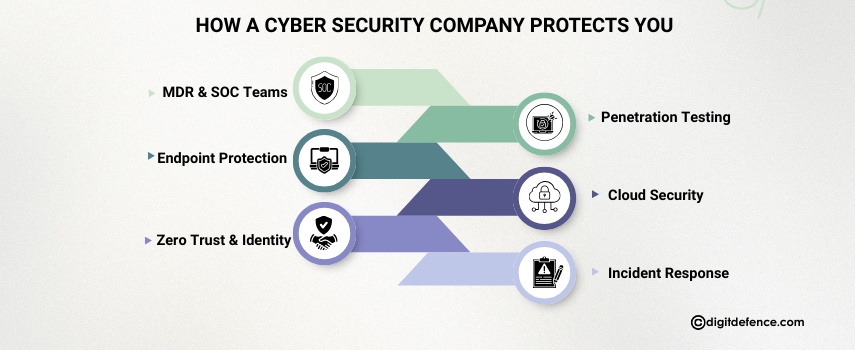
This is where partnering with a professional cybersecurity company makes a world of difference. Their job isn’t just to stop attacks but to stay ahead of them. Here’s how they do it:
Managed Detection and Response (MDR) with SOC Teams
A dedicated Security Operations Center (SOC) monitors systems around the clock. MDR combines human experts with advanced tools to spot unusual activity before it becomes a disaster.
Endpoint and Network Protection Solutions
From laptops to mobile phones to routers, every endpoint is a potential entry point. Cybersecurity providers lock these down with advanced antivirus, firewalls, and intrusion prevention systems.
Zero Trust and Identity Security Measures
Zero Trust means “never trust, always verify.” Instead of assuming employees or devices are safe, every login and action is verified. This drastically reduces the chances of insider misuse or stolen credentials.
Penetration Testing and Vulnerability Assessments
Think of penetration testing as a fire drill for your systems. Ethical hackers simulate real attacks, showing businesses exactly where they’re weak. Regular assessments help close gaps before criminals find them.
Cloud Security and Data Encryption Practices
With businesses moving to the cloud, security must follow. Cybersecurity experts ensure data is encrypted in storage and transit, making it unreadable to anyone without the right keys.
Incident Response and Recovery Planning
Even with strong defenses, incidents happen. What matters most is how fast a business responds. Security firms create playbooks that minimize downtime, recover data quickly, and keep operations running smoothly.
ALSO READ: Secure Your Business with Cyber & Network Security Steps
Importance of Compliance and Proof of Protection
In many industries, protecting data isn’t just smart, it’s the law.
Certifications and Security Audit Reports
A trusted cybersecurity company provides certifications and audit reports that prove compliance with industry standards. This isn’t just about avoiding penalties; it’s about showing customers their data is in safe hands.
Service Level Agreements and Transparency Standards
Clear SLAs ensure businesses know what level of protection and response times to expect. Transparency builds accountability and strengthens trust between provider and client.
How to Choose the Right Cyber Security Company
With so many providers out there, how do businesses decide? Here are the key factors to compare:
Evaluating Service Range and Technical Expertise
Does the provider only offer antivirus tools, or do they cover MDR, penetration testing, and cloud security? Breadth of services matters.
Comparing Response Times and Threat-Hunting Capabilities
How quickly do they detect and respond? Do they actively hunt threats or just react after an alert? Faster response often means less damage.
Assessing Costs, Scalability, and 24/7 Support
A good partner scales with your business and provides round-the-clock support. Cyber threats don’t wait for business hours, and neither should your defense.
Business Benefits of Partnering with Experts
When businesses partner with a professional cybersecurity company, the benefits are clear.
Lower Cyber Risk and Breach Probability
Advanced protection drastically reduces the chances of costly breaches.
Stronger Compliance and Customer Trust
Meeting regulations while providing security builds customer loyalty. People want to know their data is safe.
Improved Continuity and Operational Resilience
Even if something goes wrong, proper planning ensures quick recovery and minimal downtime.
Digitdefence’s Approach to Cyber Protection
Among the many providers, Digitdefence stands out with a layered and compliance-driven approach.
Layered Cybersecurity Framework for Businesses
Instead of one-size-fits-all, Digitdefence builds multi-layered strategies covering endpoints, networks, cloud, and employee training. This ensures every angle of defense is covered.
Compliance-Driven Security Solutions
From GDPR to Indian IT Act requirements, Digitdefence ensures businesses not only stay safe but also stay compliant. Their focus on regulatory alignment helps organizations avoid fines and reputational risks.
Modern cyber attacks are smarter, faster, and more destructive than ever. From AI-powered attacks to supply-chain breaches, no business is immune. But with layered protection, 24/7 monitoring, and compliance-driven strategies, businesses can stay ahead of threats. That’s exactly what a professional cybersecurity company delivers.
Digitdefence, in particular, has proven its ability to combine technology, expertise, and compliance into tailored solutions that protect businesses across industries.
Organizations are encouraged to compare providers, evaluate their strengths, and contact Digitdefence for a consultation or security audit. In today’s digital world, cyber protection isn’t just an IT expense; it’s the foundation of business survival and growth.
GET A FREE SCAN FOR YOUR BUSINESS: CLICK HERE!
REACH US: [email protected]
PHONE: +91 7996969994
