In today’s hybrid work environment, businesses face increasing challenges in securing data while enabling seamless remote access for employees. Remote Access VPNs for Business offer a critical solution by providing secure connectivity for distributed teams and protecting sensitive information from cyber threats. This guide is tailored for tech professionals, including IT managers, CTOs, and network administrators, who are tasked with selecting the best remote access VPN for their organization. By the end, you will have a comprehensive framework to evaluate and implement a VPN solution that ensures security, performance, and scalability.
Understanding Remote Access VPNs
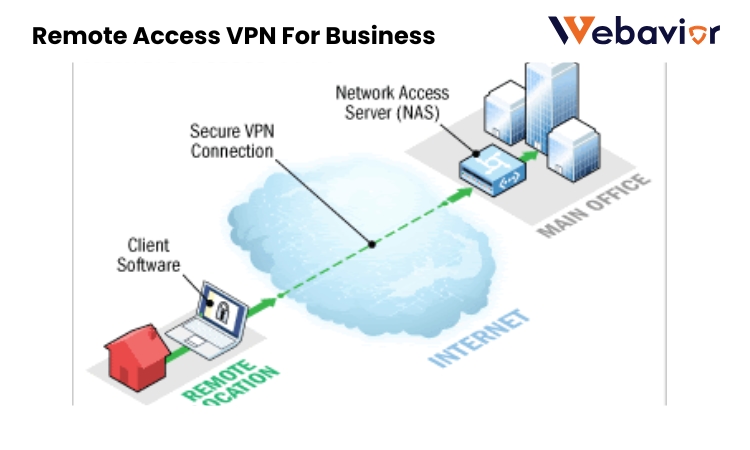
A remote access VPN allows employees to access the sensitive network of the company remotely, that is, they can connect to the businesses own network form anywhere by creating an encrypted tunnel to protect the data. In contrast to site-to-site VPNs, which link whole networks, Remote Access VPNs for Business are user focused and as such, suitable when it comes to remote and hybrid workforces. They use some protocols, and they can be OpenVPN, IPsec, or WireGuard to guarantee safe data transfer. They also allow to support authentication similar to multi-factor authentication (MFA) and integrate systems such as Active Directory. In the case of a technology professional, it is important to realize the technical underpinnings, encryption protocols such as AES-256 and client server architecture, would help assessing VPN solutions in a much better way.
Why Your Business Needs a Remote Access VPN
Security Benefits
Remote access VPNs secure important information by encrypting the connections, especially on the insecure and open public Wi-Fi networks. They avoid the leakage of information and guarantee uninterrupted work with major resources, as CRM systems or financial databases without the risk of losing information.
Operational Benefits
VPNs also contribute to productivity by facilitating the access of remote workers, and enable a BYOD policy. They enable the cooperation of teams without the need to travel across distances, and they do not undermine security, which enhances efficiency in operations.
Compliance and Risk Mitigation
VPNs help businesses comply with data protection regulations like GDPR or HIPAA by securing data in transit. They also reduce the risk of unauthorized access through robust authentication mechanisms, ensuring compliance and minimizing vulnerabilities.
Case Study
A middle-size IT company has deployed a remote access VPN to enable secure remote work of the employees, and although it did cause a 40 percent decline in data breaches, it did significantly facilitate employee access to cloud-based resources.
Key Features to Look for in a Remote Access VPN
When choosing a VPN, you should focus on the features that will improve its security, performance and usability. Comprehensive security should incorporate AES-256 encryption, multi- factor-authentication, kill switch and DNS leak protection to avoid vulnerabilities. Performance is critical and there should be high speed servers to reduce latency in the case of real-time applications. Scalability means that the VPN can scale with your workforce so it can manage higher user traffic with ease. User friendliness is paramount, having easy-to-use software interfaces to the clients and management control consoles to the IT administrator. Ability to work on multiple platforms, including windows, macOS, Linux, iOS and android, and integration with single sign-on (SSO) or Active Directory is essential. There may also be other functions such as split tunneling to optimize the bandwidth and dedicated IP addresses to support a particular use-case.
Evaluating VPN Providers: A Technical Checklist
Technical professionals should carefully consider your VPN provider. Test security and privacy by examining encryption standards and non-logging policies and consider certifications such as ISO 27001 as assurances of maximum protection. Test and evaluate performance of server reliability, latency and throughput to determine that the server is suitable to business requirements under normal workload conditions. Compare scalability and price, between per-user-pricing and flat-rate pricing models, and their ability to accommodate future expansion. Ensure that the provider gives 24/7 technical support and that there are definite Service Level Agreements (SLAs) on the uptime. Check unscrupulous vendors by reviewing what customers say about the inquiry and investigate any history of security breaches to establish reliability.
Deployment Considerations
Cloud vs. On-Premises VPNs
Cloud-based VPNs offer scalability and ease of deployment, making them suitable for dynamic businesses, while on-premises solutions provide greater control for handling sensitive data. Assessing your organization’s needs will guide the choice between these options.
Implementation Steps
Begin by assessing network requirements and user access needs to define the scope. Configure authentication policies, such as MFA and role-based access, to ensure security. Test connectivity and monitor performance after deployment to address any issues promptly.
Integration
Ensure the VPN integrates seamlessly with existing firewalls, endpoint security solutions, and identity management systems. Plan deployments during low-traffic periods to minimize downtime and ensure a smooth transition.
Training
Provide employees with clear instructions on VPN usage to encourage adoption. Train IT teams on monitoring and troubleshooting tools to maintain system reliability and address issues efficiently.
Common Challenges and Solutions
During peak use, performance bottlenecks can break the flow of operation but this can be lessened through load balancing and server selection optimization. Technical problems might reduce the level of user adoption, but the issue can be resolved through the implementation of user-friendly interfaces and training sessions. Finding the balance between usability and security is not easy, still, the split tunneling and MFA offering can strike a balance of convenience without reducing security. Adherence to regional regulations may be realized by ensuring that the provider has wide server coverage in the region and appropriate certification to address the legal compliance.
Top Remote Access VPN Solutions for Businesses
Leading Providers
A number of VPN providers are particularly viable in business. Cisco AnyConnect is an enterprise solution, and with strong integrations needed, suitable to large organizations. NordLayer offers business oriented features, bringing a simple scale-ability and user management, making it a good choice of growing companies. The Perimeter 81 is a cloud-native and zero trust solution suitable to support modern and distributed workforces.
Open-Source Alternatives
Open-source options like OpenVPN and WireGuard offer cost-effective solutions for businesses with in-house IT expertise. While they require more technical setup, they provide flexibility and robust security for cost-conscious organizations.
Best Practices for Managing a Remote Access VPN
Keep VPN software updated and patched to fix vulnerabilities and give security. Having monitoring tools allows you to monitor the frequency of use and could identify the anomaly so that you are proactive in resolving issues. Implement the least privilege principle as access control policies and perform regular audits so that unacceptable access may be stopped. Establish failover mechanisms to maintain a high availability level, and reduce the amount of disruptions. Make continuous employee training on cybersecurity good practices to further drive secure usage of VPN.
Future Trends in Remote Access VPNs
The future of Remote Access VPNs for Business is evolving with emerging technologies. Zero trust architecture is gaining traction, requiring verification for every user and device to enhance security. Integration with Secure Access Service Edge (SASE) combines VPNs with cloud-native security for comprehensive protection. AI-driven tools are optimizing VPN performance and threat detection, improving efficiency. New protocols like WireGuard are becoming popular for their lightweight design and faster connections, offering improved performance for business applications. For more information visit Webavior.
Conclusion
Business VPNs by Remote Access are critical to protect remote work and operational efficiency. Emphasizing on security, performance and scale, tech professionals can choose a VPN that best suits the need of their organization. The first step is to undertake an assessment of requirements, provider evaluation, and the piloting of a solution so that much of the deployment is successful. Visit vendor websites or enquire with technology professionals to choose a resourceful mode to fortify the remote working capacity of your business.
